Network operations management is defined as the activities performed by networking staff to monitor, manage, and respond to alerts on a network’s availability and performance. These activities are essential to ensure that the network infrastructure is running smoothly and within its optimal operating conditions.
However, defining what these optimal conditions should be isn’t so clear-cut. Third-party vendors may guide in certain areas, but in most cases, the responsibilities fall on the network operations engineers to define what these thresholds are.
The challenge is twofold: one needs to define what these thresholds are and keep them continuously updated as network conditions change over time. This is why network anomaly detection algorithms are critical — they provide a scalable, automated way to learn and maintain normal operating ranges.
The Challenge of Static Thresholds
There are usually two types of outcomes that can occur when defining these thresholds.
- Thresholds set too high may result in a false representation of the normal operating range.
- Thresholds are set too low may result in a very noisy network operation.
So, the challenge is to set and maintain a good balance that results in meaningful alerts when these thresholds are crossed.
Oftentimes, these thresholds are set based on what humans have learned over time and what we perceive to be normal or not for these metrics.
In today’s cloud era, network and IT infrastructures are more complex, and there are thousands of different metrics (with millions of time series associated) required to understand the operating state fully. It is beyond human capacity to decide what is or is not normal or abnormal at this level of complexity and scale.
This is where network anomaly detection algorithms become essential.
How Network Anomaly Detection Algorithms Help
One advantage of using algorithms is their ability to enhance our capabilities of performing job-related tasks. In this situation, network anomaly detection algorithms can be used to learn what is normal or not for each of the thousands of metrics or millions of time series separately.
Essentially, these algorithms are based on the same learning mechanisms we use by referencing historical data.
Selector’s platform integrates algorithms to learn from the past and to help identify what the normal operating conditions are. In doing so, the algorithms dynamically set these thresholds to values that are representative of the behavior of these metrics.
When thresholds are crossed, this suggests that an anomaly has occurred and requires further investigation.
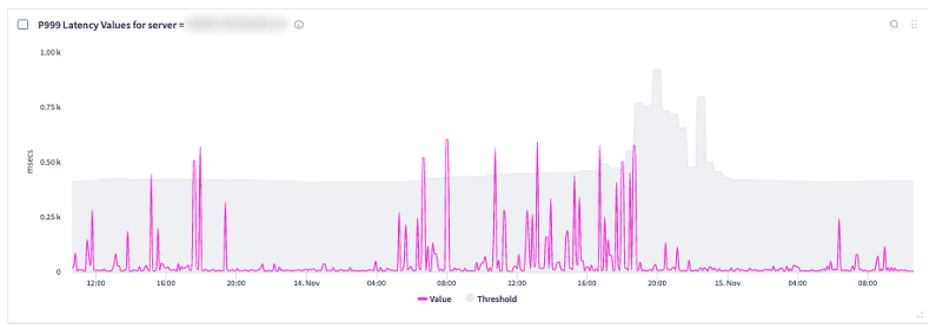
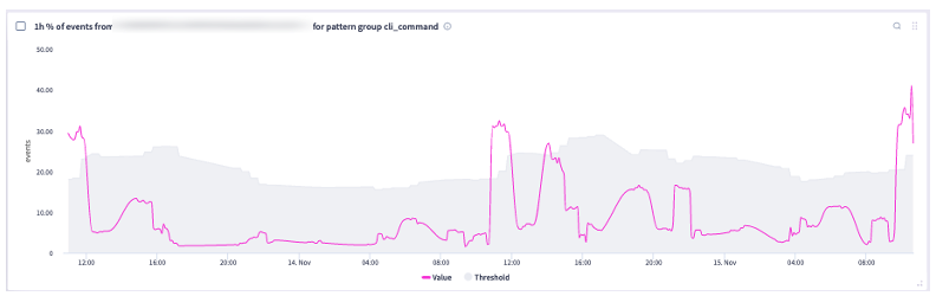
Selector’s Auto-Baselining for Anomaly Detection
Selector’s auto-baselining algorithm computes, in real time, the dynamic threshold for each time series. It accomplishes this by looking at:
- Short-term past (usually a few hours) representing current dynamic behavior.
- Long-term past (usually a few weeks) captures seasonal patterns that determine the expected operating range based on time-of-day or day-of-week trends.
By combining short-term and long-term history, Selector’s algorithm determines the normal operating range and adapts as conditions evolve.
Once anomalies are detected, they can be correlated with:
- Other anomalies in the system
- SNMP traps
- Syslog messages
- Structured events from third-party apps
- Configuration changes
Alerts can then be configured and turned into incidents in the end user’s ticketing systems.
Reducing Alert Fatigue with Network Anomaly Detection Algorithms
Setting static thresholds should be limited to a few key metrics where operating boundaries are well known.
For everything else, network anomaly detection algorithms — such as Selector’s auto-baselining — provide the accuracy and real-time adaptability needed to:
- Reduce false positives and alert fatigue
- Detect anomalies faster
- Improve operational efficiency
Benefits of Selector’s Algorithm-Driven Analytics
Let’s explore some of the benefits of the Selector Analytics platform:
- Operations teams no longer need to create and maintain static thresholds.
- Dynamic thresholds are continuously computed and updated based on real behavior.
- Reduces alert fatigue by minimizing false positives from manual thresholds.
See Network Anomaly Detection Algorithms in Action
Below are several screenshots of this unique feature:
Interested in learning more about this feature? Contact us today for a free demo!