PLATFORM • ANOMALY DETECTION

Detect abnormal system behavior
Real-time anomaly detection provides valuable insights so you can take immediate action.
Isolating issues or waiting for a ticket isn’t enough. Comprehensive anomaly detection powered by machine learning delivers proactive identification of system problems. So, you can drill down to their root causes before they become incidents or outages.
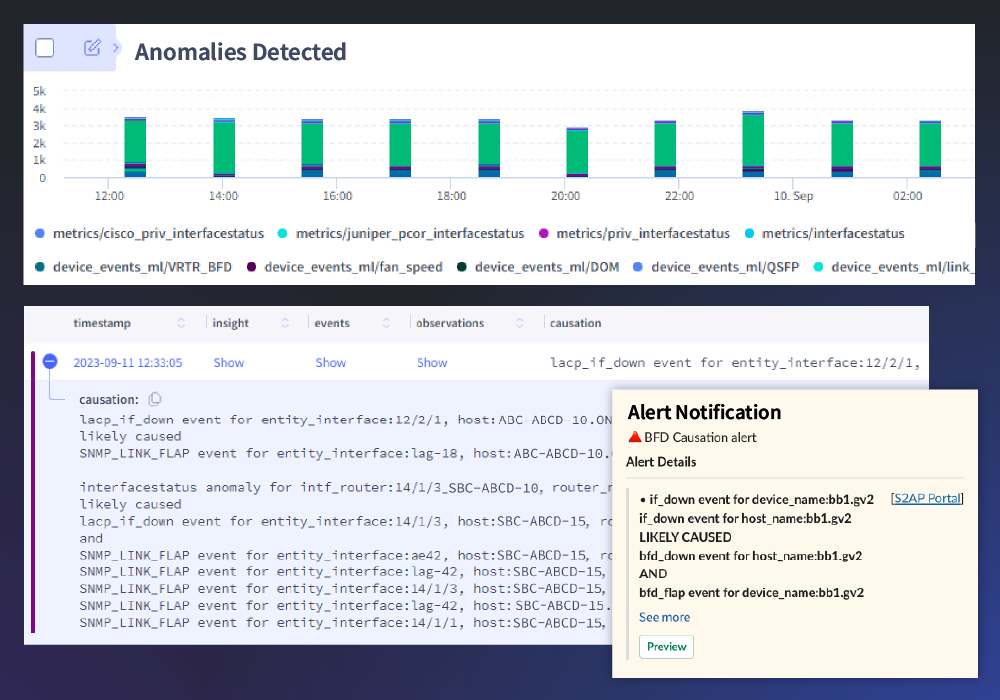
Track what’s normal and respond to what’s not
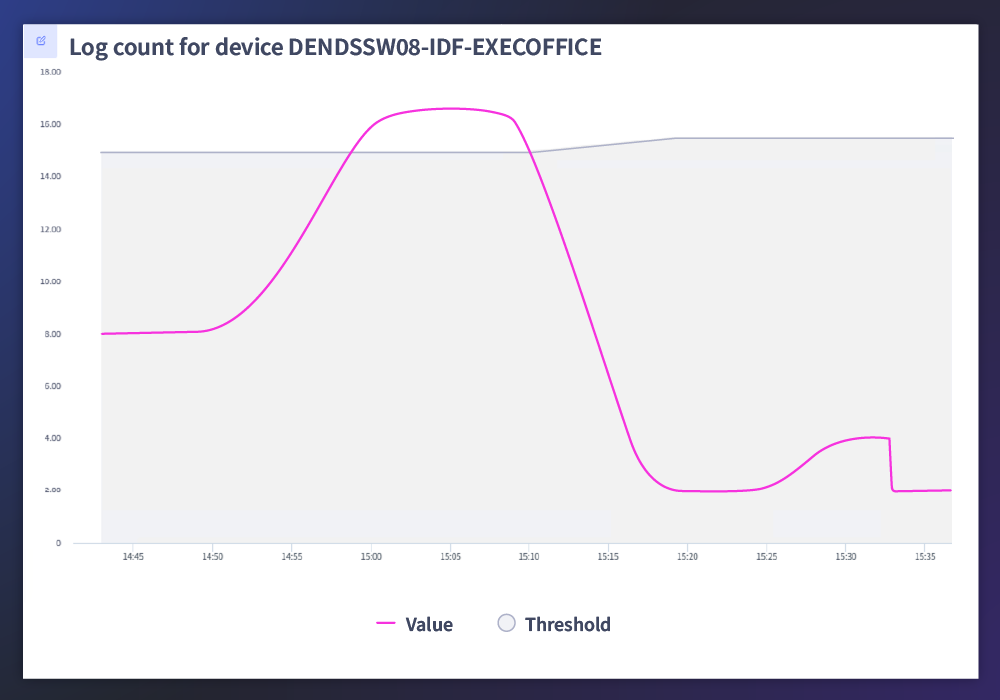
Monitor your way
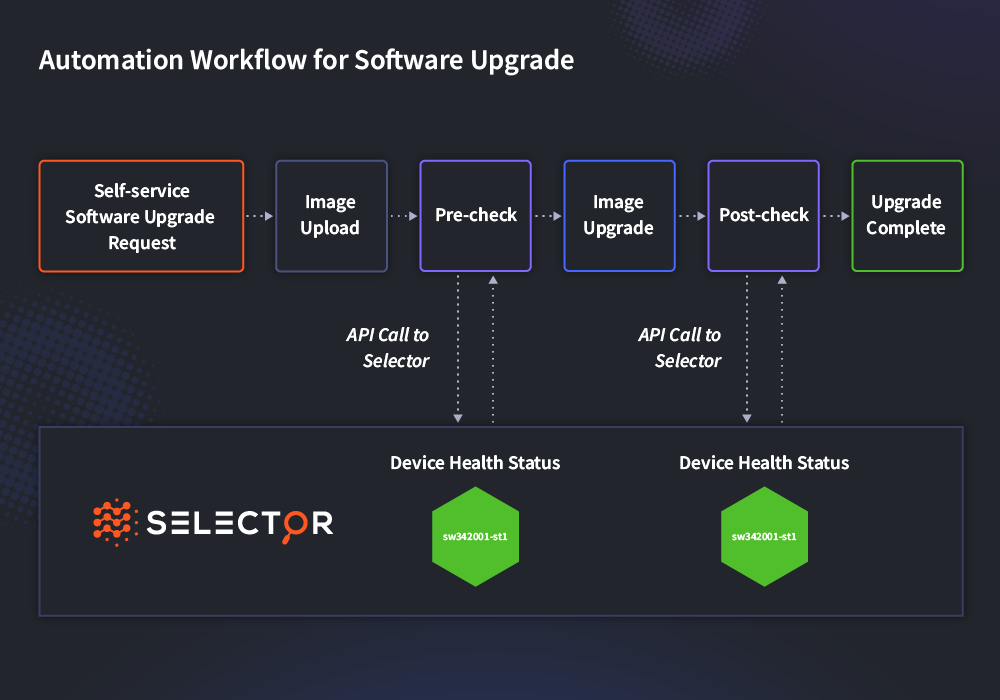
Prevent customer-impacting issues
Absolutely fantastic company. Their approach to intelligent network monitoring and analytics is unique and refreshing.
I can’t recommend them highly enough. I honestly get excited by weekly catch-up calls because of the possibilities
Andrew Neiberger
Principal Engineer
Comcast

Anomaly Detection: An Expert View
Networking industry leader Javier Antich highlights the efficiency benefits of anomaly detection in a recent blog.